External Identity Provider SSO with Pangolin
Managing access to applications across different networks and clouds is often messy. Traditional reverse proxies get scattered in different places, each with its own login logic and credentials. Maintaining them means duplicating authentication and policies everywhere.
Pangolin simplifies this. It provides a centralized, managed proxy layer:
- Secure tunnels to any environment such as a datacenter, office, IoT device, or multi‑cloud.
- Apps exposed in the browser without VPN clients.
- Identity and access control managed from one dashboard.
Because Pangolin becomes the front door for your apps, Single Sign‑On (SSO) is essential. Users should log in once with the accounts they already use, and admins should be able to manage access from a single source of truth.
That’s why Pangolin Cloud now supports Google Workspace and Microsoft Entra ID (Azure AD) as native identity providers, alongside any OAuth2/OIDC system.
Why this matters
Supporting identity providers directly in Pangolin Cloud unlocks three key benefits:
- Single Sign-On (SSO): Your team logs in once with their existing account and seamlessly gains access to Pangolin resources, without managing a new set of usernames and passwords.
- Centralized identity management: Because authentication runs through your IdP, you can manage access in one place. Disable a user in Google Workspace or Microsoft Entra, and their access to Pangolin is cut off immediately.
- Consistent security policies: Enforce MFA, conditional access rules, and compliance requirements across Pangolin just as you do for the rest of your stack.
With auto-provisioning, new users can be created automatically in Pangolin at first login and assigned roles based on your IdP’s group or attribute data. No more sending invites or chasing people down to set passwords because your IdP remains the single source of truth.
How this helps in practice
Pangolin acts as an identity-aware proxy: a central point through which you can expose internal applications securely over the internet, while managing who can access what. With IdP support in the cloud, this becomes even more powerful.
Imagine you’re exposing an internal admin dashboard, developer tooling, or a legacy web app through Pangolin. Instead of maintaining a separate login system or manually handling user credentials, you can require authentication through your existing provider. A contractor logging in with their company Google Workspace account only sees the apps they’ve been granted, while everyone else is automatically blocked. When that contract ends, disabling their Google account instantly revokes their access to Pangolin too.
For organizations running hybrid environments, this provides a consistent way to secure applications no matter where they live — on-prem, in the cloud, or on a developer’s laptop. And because Pangolin handles access at the proxy layer, you get unified visibility and control across your network without having to retrofit every app with custom authentication.
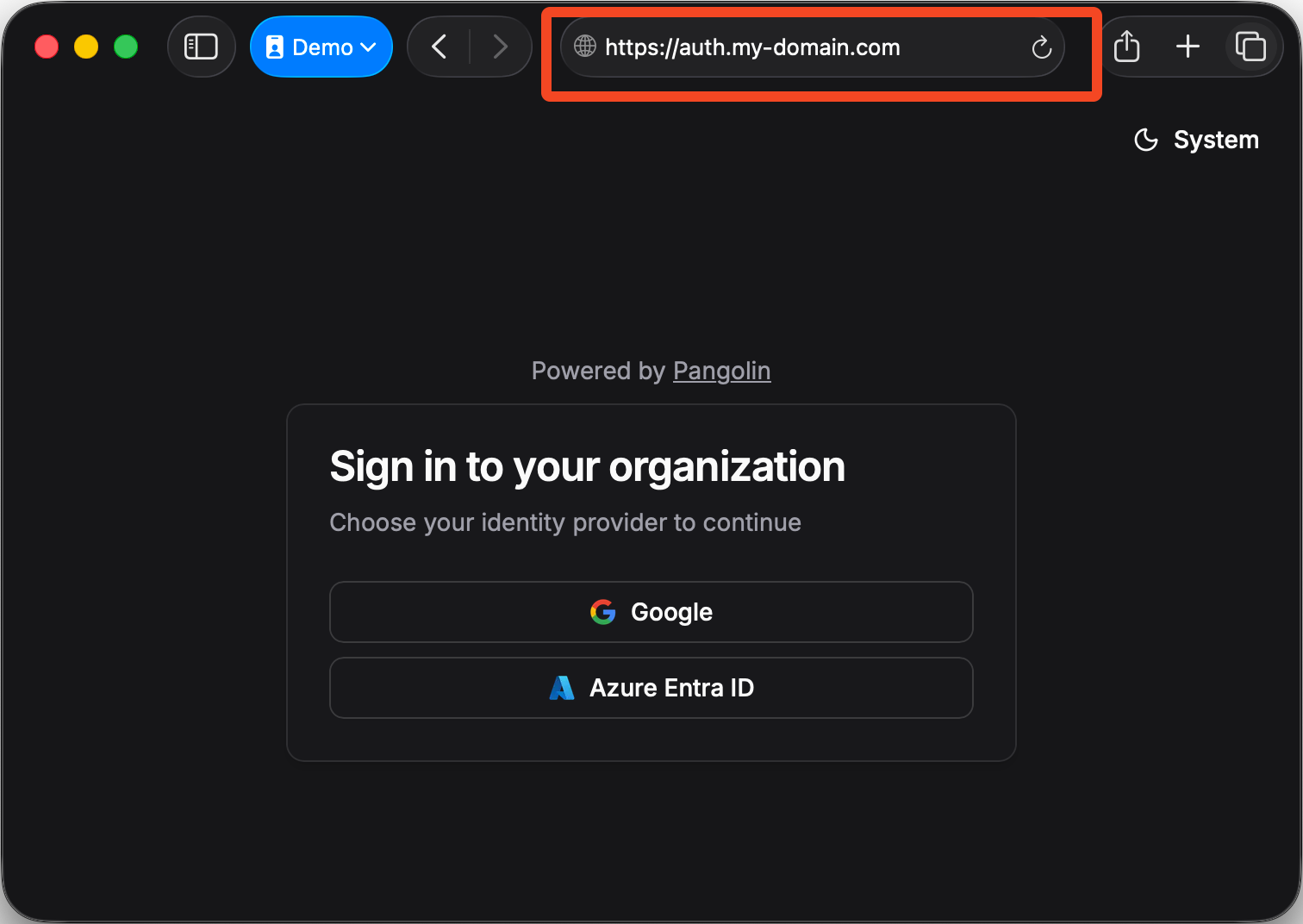
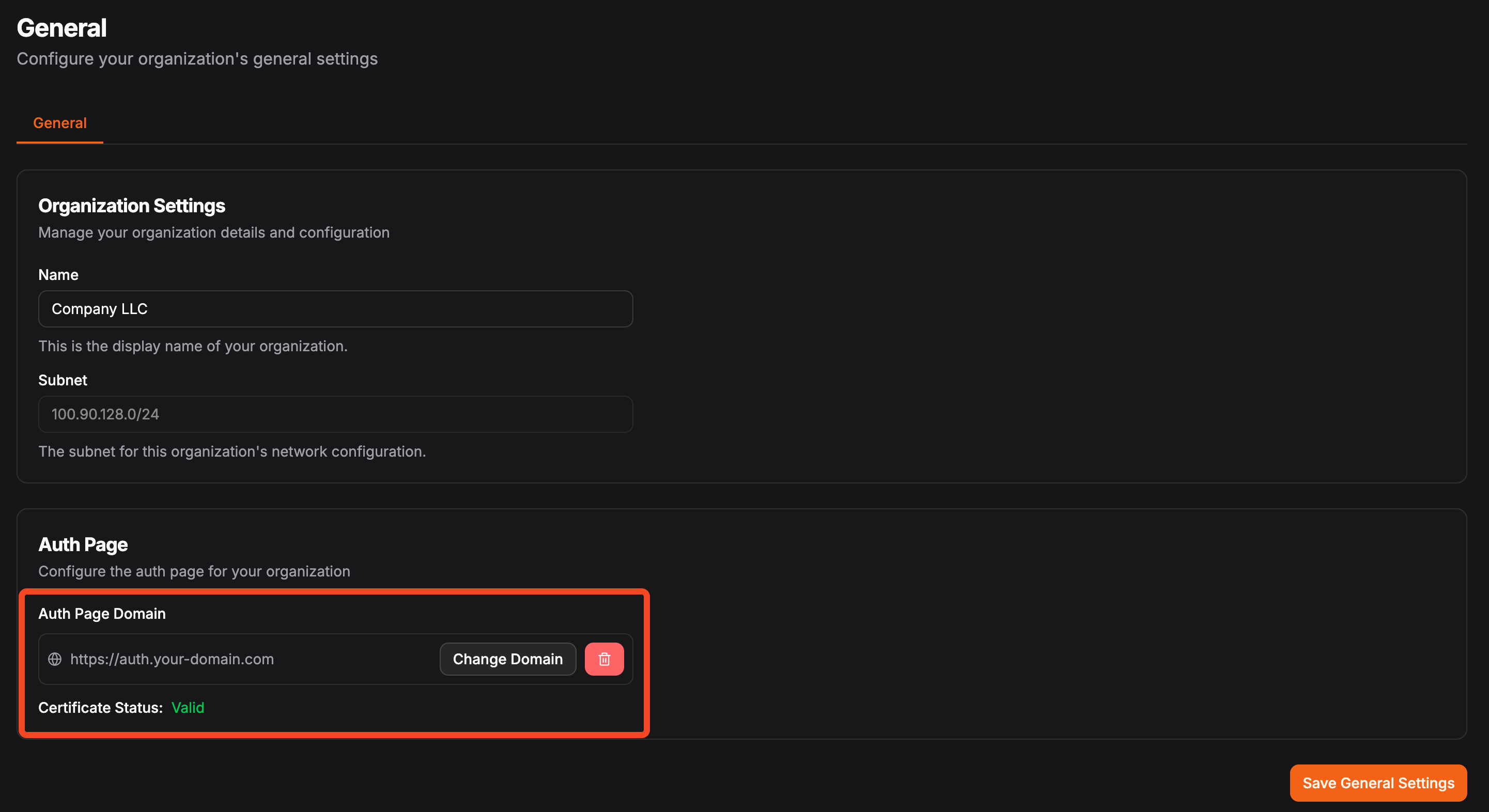
Custom domains for authentication
Alongside identity provider support, we’ve also added a new feature that lets organizations set a custom domain for their authentication page. This is the page users see whenever they log in to access a Pangolin-protected resource or the Pangolin management dashboard. With a custom domain, users encounter a URL that matches your organization’s brand which increases trust and reduces confusion.
Instead of being redirected to a generic login, your team might see something like auth.yourcompany.com each time they authenticate. This reinforces that access is sanctioned by your organization and makes the login process more familiar. It’s especially valuable when giving access to external collaborators or contractors: the domain signals that they’re logging in through your systems, not a third party.
You can configure this custom domain directly in the Organization Settings page in the dashboard.
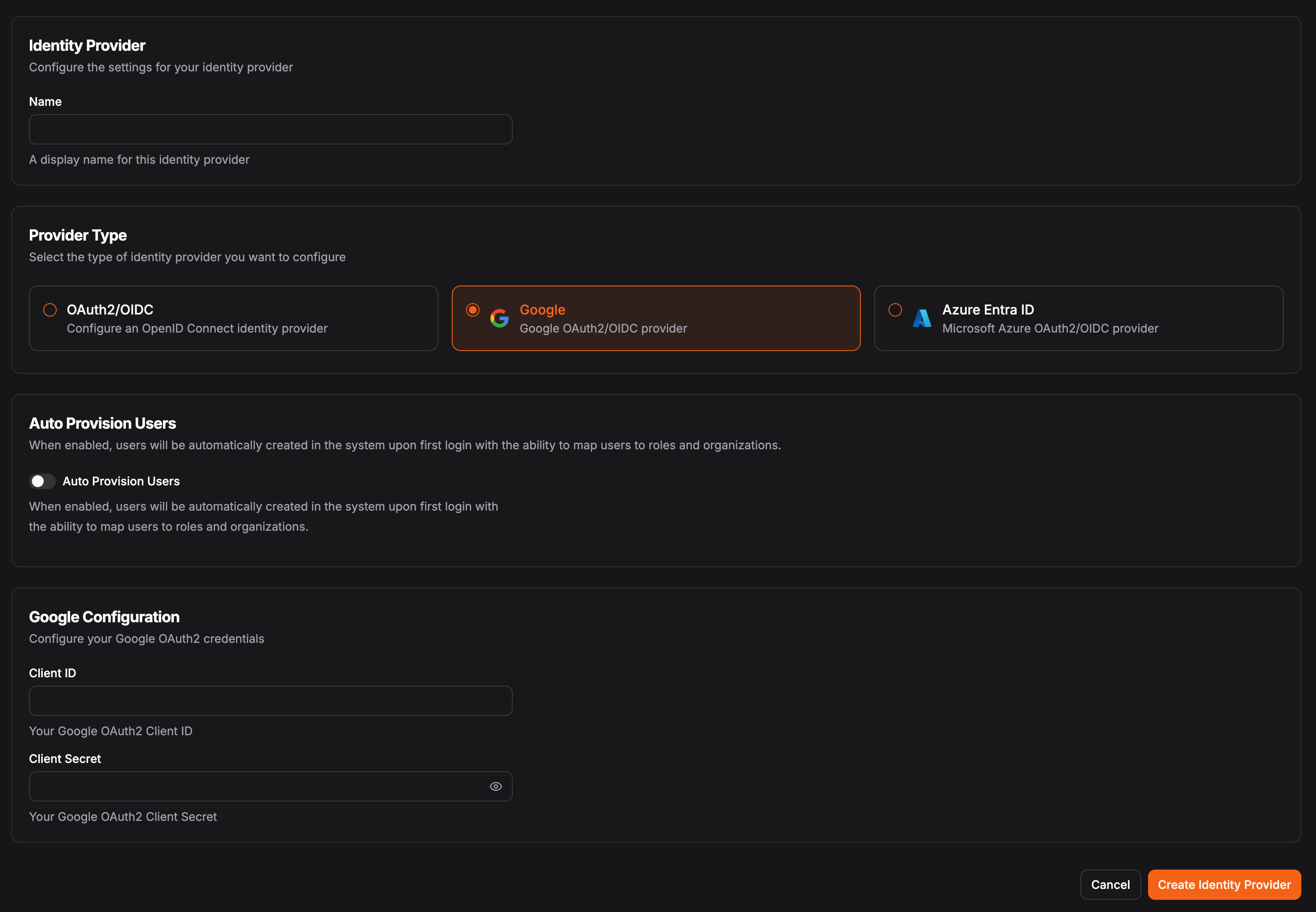
Native Google and Microsoft integrations
While Pangolin supports any OIDC-compliant provider, we’ve gone further with dedicated integrations for Google and Microsoft Entra ID. These make setup even simpler, with configuration flows purpose-built for the ecosystems most teams are already using.
- Google Workspace integration: Ideal if your organization already relies on Gmail, Calendar, or Google Docs. Users authenticate directly with their existing Google accounts for seamless access to Pangolin Cloud.
- Microsoft Entra ID integration: Perfect for enterprises standardized on Microsoft 365 or Azure services. Leverage your existing Active Directory groups to grant and revoke access automatically.
We’ve also put together short demo videos to walk through both setups:
Google login with Pangolin Cloud
Microsoft Entra ID login with Pangolin Cloud
Dive deeper
If you’re ready to try it out, we’ve documented the full setup process:
We’re excited to keep expanding how identity integrates with Pangolin. Give it a try and let us know how it works for your team.


